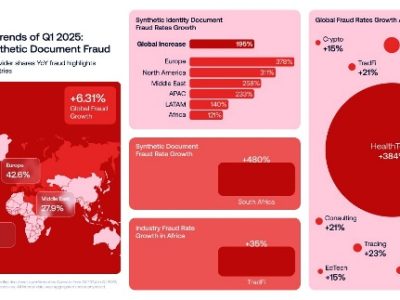
Group-IB, a global cybersecurity leader specializing in the investigation and prevention of cybercrimes, has published its new report Hi-Tech Crime Trends 2022/2023, the latest edition of the company’s annual round-up of the most pertinent global cyber threats. In the report, Group-IB Threat Intelligence analysts reveal how ransomware operations remained the top cyber threat to companies and organizations across the world between H2 2021 and H1 2022, not least in the Middle East and Africa (MEA).
RELATED: Check Point Research records 38% increase in 2022 global cyberattacks
According to Group-IB’s research, the number of companies that had their information uploaded onto dedicated leak sites (DLS) between H2 2021 and H1 2022 was up 22% year-on-year to 2,886, which corresponds to eight companies having their data leaked online every single day. In the MEA region, 150 companies had their information leaked on DLS during the reporting period.
For the second consecutive year, Group-IB researchers observed the increasing impact of initial access brokers (IABs) on the ransomware market in MEA and beyond. Group-IB researchers detected 2,348 instances of corporate access being sold on dark web forums or privately by IABs, twice as much compared to the preceding period. The number of brokers also grew from 262 to 380, leading to a drop in prices that made the attacks of ransomware gangs and other threat actors more affordable. In the MEA region, the number of network access offers more than doubled to 179 in H2 2021 – H1 2022, resulting in a drop in price of total offers of 23%.
For the 11th consecutive year, the Hi-Tech Crime Trends report analyzes the various aspects of the cybercriminal industry’s operations, examines attacks, and provides forecasts for the threat landscape for various sectors such as the financial industry, telecommunications, manufacturing and energy. Each year, Group-IB presents a comprehensive overview of the global threat landscape and our researchers share their predictions for what lies ahead. Group-IB’s hands-on experience in investigating cybercrime as well as its innovative suite of products and services help to describe all underground trends and activities that are worth watching and even make long-term predictions that help cybersecurity teams around the world to tailor their cyber defense.
A devil’s ransom
Across the globe, 2,886 companies had their information, files, and data published on DLS in H2 2021 – H1 2022, a 22% increase compared to the 2,371 companies affected during the previous period (H2 2020 – H1 2021). As with the preceding year, the number of ransomware-related data leaks peaked in the final quarter of 2021, when the data of 881 companies was shared on dedicated leak sites. It is important to note that the actual number of ransomware attacks is believed to be significantly higher as many victims chose to pay the ransom and some ransomware gangs do not use DLS.
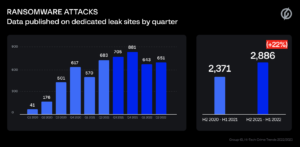
Figure 1: Number of global ransomware-related data leaks per quarter (Q1 2020 – Q2 2022)
“It is worth noting that the number of victims whose data was published in the wake of ransomware attacks in H2 2020 – H1 2021 was 935% up from the preceding year. As a result, the 22% year-on-year growth seen in the observed period suggests that the Ransomware-as-a-Service market has passed the phase of rapid growth and is now beginning to stabilize,” says Dmitry Volkov, CEO at Group-IB.
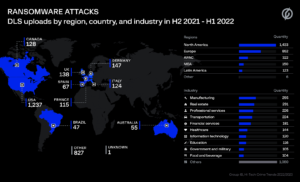
Figure 2: Global ransomware-related data leaks by region (H2 2021 – H1 2022)
Group-IB discovered that companies based in North America (50% of companies whose data was leaked by ransomware gangs) were the most affected by ransomware-related data leaks. Comparatively, the MEA region was the second-least affected by ransomware-related data leaks, as 150 companies from the region had their data published online. Only 5.3% of the leaks on DLS contained data from countries from this region. The most affected countries were Israel (23 companies), South Africa (21), Turkey (14), United Arab Emirates (14), and Saudi Arabia (12).
Other affected countries in Africa were: Egypt (6 companies), Morocco (3 companies), Angola (2 companies), Botswana (2 companies), Nigeria (2 companies), Zambia (2 companies), Côte D’Ivoire (2 companies), and Burkina Faso, Congo, Ethiopia, Mali, Senegal, Tanzania, Tunisia (all 1)
The most active ransomware gang in the MEA market was Lockbit, responsible for 37% of publications of victims’ data from the region on designated leak sites. Second in this list was Conti, a Russian-speaking ransomware group that launched the devastating ARMattack campaign at the end of 2021, which was responsible for 12% of leaks, and third was Hive (4% of leaks).
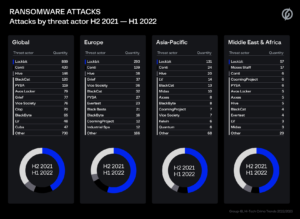
Figure 3: Ransomware-related data leaks H2 2021 – H1 2022 by threat actor
Group-IB’s analysis of the threat posed by ransomware gangs also revealed that globally, the largest number of ransomware-related data leak victims were found in the following sectors: manufacturing (295 companies), real estate (291), professional services (226), and transportation industries (224). In the MEA region, 18 financial services companies, 12 manufacturing companies, 7 energy companies, 3 telecommunications companies, and 3 IT companies had their files published on DLS by cybercriminals.
In the reporting period, the number of ransomware attacks on companies in the manufacturing sector worldwide increased by 19% compared to the previous period (H2 2020-H1 2021) to 295. Similar increases were observed in the energy industry (up 43% to 80), financial organizations (up 43% to 181), and the IT sector (up 18% to 120). Interestingly, attacks on telecommunications companies dropped 15% year-on-year to 29.
“Ransomware is likely to remain the major threat for business and governments across the globe in 2023,” says Dmitry Volkov, CEO at Group-IB. “Ransomware gangs have been able to craft a stable market for their criminal enterprises, and the ransom demands issued to companies once they have been attacked are continuing to rise rapidly. Many of the most prominent ransomware gangs have turned into criminal start-ups. They have a rigid hierarchy and bonuses for overachievement. While the growth trends might slow down, it is likely that the ransomware market could consolidate further, continuing a trend seen in H2 2021 – H1 2022.”
InsatIABle appetite
During the period from H2 2021 to H1 2022, Group-IB’s Threat Intelligence unit analyzed underground advertisements describing compromised networks and detected 2,348 instances of corporate access being offered for sale — twice as much as during the previous period (1,099 access offers). Among these, 2,111 offers contained information about the country, and 1,532 specified the victim’s industry.
Initial access brokers have significantly expanded their presence worldwide. The number of countries where they broke into corporate networks increased by 41%: from 68 to 96 during H2 2021 – H1 2022. Just like last year, US-based companies were the most popular commodity among the initial access brokers, with almost a quarter of all discovered access offers related to US companies (558). Similarly to last year, the industries most affected by IABs were manufacturing (5.8% of all companies), financial services (5.1%), real estate (4.6%), and education (4.2%).
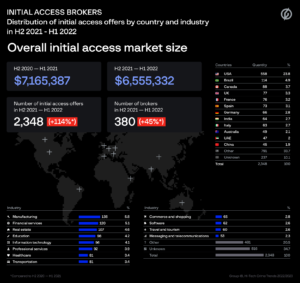
Figure 4: Overview of IAB trends (H2 2021 – H1 2022)
“Initial access brokers play the role of oil producers for the whole underground economy,” says Dmitry Volkov. “They fuel and facilitate the operations of other criminals, such as ransomware and nation-state adversaries. As access sales continue to grow and diversify, IABs are one of the top threats to watch in 2023. Private and public companies in the MEA region should consider setting up a threat intelligence program to monitor for compromised credentials of their workforce.”

Figure 5: IAB market size & offers in MEA (H2 2021 – H1 2022)
Group-IB’s analysis of the threat posed by ransomware gangs also revealed that globally, the largest number of ransomware-related data leak victims were found in the following sectors: manufacturing (295 companies), real estate (291), professional services (226), and transportation industries (224). In Europe, most victims posted on the DLS were conducting business in the manufacturing (104), IT (37), and financial (35) sectors.
“Ransomware is likely to remain the major threat for businesses and governments across the globe in 2023,” says Dmitry Volkov. “Ransomware gangs have been able to craft a stable market for their criminal enterprises, and the ransom demands issued to companies once they have been attacked are continuing to rise rapidly. Many of the most prominent ransomware gangs have turned into criminal start-ups. They have a rigid hierarchy and bonuses for overachievement. While the growth trends might slow down, it is likely that the ransomware market could consolidate further, continuing a trend seen in H2 2021 – H1 2022.”
Stealing the limelight
One of the most notable changes to the global threat landscape is the increasing popularity of logs obtained with the use of information stealers — malware that gathers personal details from the user’s browser metadata. These stealers can obtain credentials, bank cards, cookies, browser fingerprints, etc. Group-IB found that between July 1, 2021 and June 30, 2022, over 96 million logs were offered for sale, with most of the compromised data coming from US users (80%), with the UK (5.4%), India (4.6%), Indonesia (2.4%), and Brazil (2%) trailing behind.
Group-IB experts discovered over 400,000 Single Sign-On logs among these 96 million logs. SSO is a widely used corporate authentication method that uses a single pair of credentials to obtain access to multiple services, making them highly sought after by cybercriminals as they allow them to get into several systems at a time with little effort. As discovered by Group-IB researchers, the threat actor behind the recent attack on Uber purchased stealer logs on one of the underground marketplaces for $20. These logs contained SSO credentials of at least two Uber employees.
“It is quite concerning what a cybercriminal with $20 and modest technical skills is capable of these days,” says Dmitry Volkov. “With remote work and SSO services becoming more prevalent, instances of access to corporate networks started appearing in stealer logs more often. Attacks on companies through their employees will become one of the main infection vectors. A silver bullet against such attacks doesn’t exist. This trend highlights the need for companies to improve their cybersecurity across all layers, including training employees to respond to social engineering, enhancing detection and response capabilities, and of course, monitoring the cybercriminal underground for compromised employee records and offers to sell access to their networks.”
About Hi-Tech Crime Trends report
Group-IB has been presenting its annual reports since 2012, integrating data gathered as a result of the company’s own investigations with incident response findings worldwide. Serving as a practical guide for a wide range of experts — in risk management, digital business transformation, strategic planning in the cybersecurity field and investing in information system protection — the report provides annual forecasts that have always proved to be accurate. For technical specialists, including СISOs, SOC and DFIR teams, researchers and malware analysts, as well as Threat Hunting experts, Group-IB’s report provides an opportunity to analyze the relevance of cybersecurity policies, adjust security settings for their systems and strengthen their expertise in countering cyberthreats relevant to their industry. Thanks to the use of unique tools for tracking the infrastructure of cybercriminals, as well as a thorough study of research by various cybersecurity teams worldwide, Group-IB experts annually identify and confirm common patterns that form a full picture of the development of cyberthreats in the world. This forms the basis of future forecasts set out in the report that help companies around the world build effective cybersecurity strategies based on relevant threats.
More analytics on Group-IB’s research hub