Check Point researchers uncover a large-scale Android adware campaign that silently drains resources and disrupts normal phone use through persistent background activity.
Check Point researchers identified a network of Android applications on Google Play masquerading as harmless utility and emoji-editing tools. Behind their cheerful icons, these apps created a persistent background advertising engine – one that kept running even after users closed or rebooted their devices, quietly consuming battery and mobile data.
RELATED: Kaspersky warns of Android malware exhibiting diverse features
At its peak, the campaign, now dubbed “GhostAd”, included at least 15 related apps, five of which were still available on Google Play at the start of our investigation.
Approximately 75% of targeted users appear to be from East and Southeast Asia, particularly the Philippines, Pakistan, and Malaysia with a smaller portion from other nearby countries and across Europe, Africa and Israel. This pattern is most likely a reflection of users who have downloaded these kinds of free “utility” apps, rather than an intentional choice by the operator.
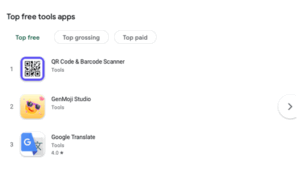
Together, these apps accounted for millions of downloads, with one reaching the #2 position in Google Play’s “Top Free Tools” category.
Despite their wide reach and intrusive behavior, the apps remained available on Google Play at least since early October, continuing to attract new downloads. Users quickly began leaving reviews describing problems such as persistent pop-up ads, vanishing app icons when attempting to uninstall, and devices becoming slower or less responsive.


Update From Google
After we notified Google about these applications, the company confirmed that all of the identified apps had been removed from the Google Play Store – some prior to our notification and others as a direct result of it. Google Play Protect, which is on by default on Android devices with Google Play Services, automatically disables the identified apps for users who have them installed, regardless of the download source.
How GhostAd Works
1. Persistent Execution via Foreground Service
The persistence begins the moment the app launches. GhostAd apps register a foreground service that ensures continuous execution – even if the user closes the app or reboots the phone.
To comply with Android’s requirements, the service displays a blank, unremovable notification, making it technically legitimate but effectively invisible.
Manifest
<service android:name=”ForegroundAdService” android:exported=”false” android:foregroundServiceType=”dataSync”/>
The “Invisible” Notification Trick
Every Android foreground service must display a notification. GhostAd apps exploit this rule by presenting a blank, constant notification – a visual placeholder that hides their ongoing ad operations.
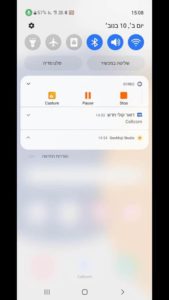
No title. No message. Just a silent indicator that something is running, but the user can’t remove it or tell what it does.
This small technicality turns a security requirement into an obfuscation tactic.
2. JobScheduler: Self-Healing Ad Engine
To reinforce the service, the apps use a JobScheduler that re-triggers ad-loading tasks every few seconds.
Even if Android terminates the service, the scheduler restarts it almost immediately – ensuring that ad requests continue nonstop.
AdJobScheduler
// AdJobSchedulervoid scheduleAdJob(Context ctx) { JobScheduler js = (JobScheduler) ctx.getSystemService(“jobscheduler”); JobInfo job = new JobInfo.Builder(4242, new ComponentName(ctx, “AdJobService”)) .setMinimumLatency(2500L) .setOverrideDeadline(5000L) .build(); js.schedule(job);}
Together, these two mechanisms create a self-healing loop that’s nearly impossible for an average user to stop.
3. The Endless Ad Loop
GhostAd integrates multiple legitimate advertising software development kits (SDKs), including Pangle, Vungle, MBridge, AppLovin, and BIGO, but uses them in a way that violates fair-use policies. Instead of waiting for user interaction, the apps continuously load, queue, and refresh ads in the background, using Kotlin coroutines to sustain the cycle.
// we.i.a.a.d.invokeSuspend()while (CoroutineScopeKt.isActive(coroutineScope)) { List<BdgtsPksjd> adList = xe.i.f().m(qgj.dgb.knb.a.j.a(false)).b().m(); if (!adList.isEmpty()) { k.l(adList); // Process new ads } DelayKt.delay(6000L, this); // Wait 6 seconds, repeat forever}
This design quietly generates ad impressions and revenue, all while draining device resources. For users, it means a hotter phone, shorter battery life, and higher data bills – even when the phone appears idle.
User Experience: “It Takes Over Your Phone Like a Virus”
As always, the user reviews told the real story. Across multiple listings, frustrated users described how the apps flooded their phones with invisible activity and constant interruptions:
“It’s the worst app I’ve ever used – it disturbs my privacy and takes over other apps for ads.”
“Do not install this app! It will block you from using your phone with annoying pop-ups every 10 seconds.”
“WORST APP EVER. It disappears when you try to uninstall it, while pouring lots and lots of ads in your phone.”
These comments highlight the hidden persistence that defines the GhostAd campaign — adware that doesn’t just display ads but embeds itself deeply into the system, running long after the user thinks it’s gone.


Impact on Users
The GhostAd campaign causes noticeable device disruption even without stealing data or showing classic malware behavior.
It quietly hijacks system resources for ad delivery, leading to performance and usability issues reported by real users.
Key impacts:
- Battery Drain: Persistent foreground services and job schedulers keep the CPU awake indefinitely, reducing battery life.
- User Deception: Hidden icons and blank notifications disguise the apps’ presence, making removal difficult.
- Reduced Performance: Constant background processes slow down other apps and degrade responsiveness.
Why It Matters
GhostAd demonstrates how legitimate advertising infrastructure can be repurposed into a large-scale abuse network – no exploits required.
By chaining foreground services, job schedulers, and continuous ad refresh, the operators created an invisible ad-farm inside users’ phones, generating profit while degrading the device experience. This campaign also underscores the ongoing challenge of detecting gray-zone threats on official app stores.
Application as we detected doesn’t need “hacking exploits” to be dangerous – it has all it needs to quietly turn the phone of a user into a data siphon. With constant internet access, the ability to run in the background after every reboot, and permissions to read and write external storage, it can systematically scan shared folders, downloads, exported documents, backups, and media-including files that originate from the corporate environment, such as reports, PDFs, logs, screenshots, exported chats, etc.-and exfiltrate them to a remote server without the user noticing. On top of powerful advertising and tracking permissions, it can build a detailed profile of the device and its owner, link the identity across services and app stores, and establish and maintain a long-lived connection back to an attacker-controlled backend. In short: without any access to SMS, contacts, or a camera, this “legitimate” app can silently sit on an employee’s device and continuously leak sensitive organizational data that was copied, downloaded, or synced to the device, giving some untrusted actor in the dark a persistent, low-friction window into your company’s information.
How to Stay Safe
- Avoid installing apps with vague names or excessive permissions.
- Always check user reviews — if you see warnings like “don’t install,” “this app acts like a virus,” or consistently low ratings, it’s best to stay away.
- Be wary of persistent blank notifications — they often hide background services.
- Regularly check Settings → Apps for unfamiliar apps that don’t appear on your home screen.
Conclusion
The GhostAd campaign blurs the line between marketing and malware. It shows how everyday advertising tools, when combined with persistence and obfuscation, can quietly undermine user trust in mobile ecosystems.
Millions of Android users unknowingly became part of a hidden ad network, their phones repurposed to generate revenue at their expense.
As mobile threats evolve, so do the creative abuses of legitimate SDKs. GhostAd is a reminder that not every threat hides in the shadows – some sit openly in the app store, disguised as harmless fun.

Indicators of Compromise (IOCs)
- 7185a439005033b45b48294b302973898e68d8c898003f98acc275b27948ad40
- a039c862807a14482169db0db5904749b7e5d733807418430d1cc3c2e3724f96
- ebd4365923964218caa24c9f88f009aefa7f1427a20f0f02927c98285734dae5
- 13805e77fb44a5a5af829f13ee494b9cfc4d5c9b470d51014cd506bd40c57426
- 91eb6afb903b2155246cb64289b4c2554922e0472fb355091843e0138c91a114